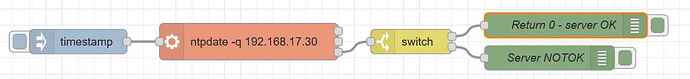
You can do that with your original exec node but instead of parsing whatever text it outputs, check the return code.
[{"id":"e19cf3ec21f8e946","type":"inject","z":"142f935612b6e391","name":"","props":[{"p":"payload"},{"p":"topic","vt":"str"}],"repeat":"","crontab":"","once":false,"onceDelay":0.1,"topic":"","payload":"","payloadType":"date","x":100,"y":100,"wires":[["52b29840836eea79"]]},{"id":"52b29840836eea79","type":"exec","z":"142f935612b6e391","command":"ntpdate -q 192.168.17.30","addpay":"","append":"","useSpawn":"false","timer":"","winHide":false,"oldrc":false,"name":"","x":310,"y":100,"wires":[[],[],["da74aeb612ae8435"]]},{"id":"da74aeb612ae8435","type":"switch","z":"142f935612b6e391","name":"","property":"payload.code","propertyType":"msg","rules":[{"t":"eq","v":"0","vt":"num"},{"t":"neq","v":"0","vt":"num"}],"checkall":"true","repair":false,"outputs":2,"x":510,"y":100,"wires":[["c55a52eb20cb4065"],["7480e1450b3a5032"]]},{"id":"c55a52eb20cb4065","type":"debug","z":"142f935612b6e391","name":"Return 0 - server OK","active":true,"tosidebar":true,"console":false,"tostatus":false,"complete":"payload.code","targetType":"msg","statusVal":"","statusType":"auto","x":700,"y":80,"wires":[]},{"id":"7480e1450b3a5032","type":"debug","z":"142f935612b6e391","name":"Server NOTOK","active":true,"tosidebar":true,"console":false,"tostatus":false,"complete":"payload.message","targetType":"msg","statusVal":"","statusType":"auto","x":680,"y":120,"wires":[]}]
Before you posted "I [only] want to make sure ..." I was going to suggest a modified Bash command to filter out unwanted text before it gets to Node-red:
ntpdate -q 192.168.17.39 2>/dev/null | sed -e /^server.*/d -e s/\ ntpdate.*//