Dashboard - Multi User Login System Flow Example
Demo - https://dashboard-muls.no-fs.com/ui/
Username=admin / Password=password
Resets changes every hour so if someone messes it up just try agin in an hour.
Requires nodes - node-red-contrib-twin-bcrypt & node-red-contrib-moment. You will need to add these nodes to your pallet.
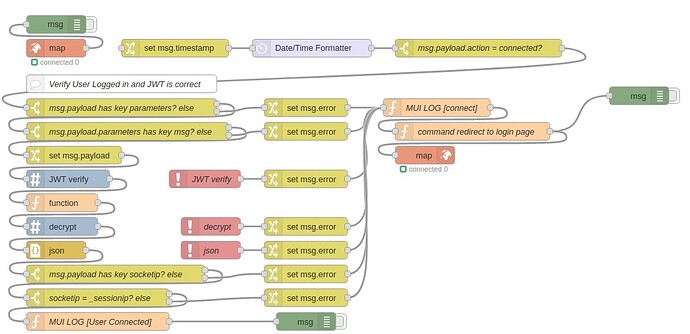
Link to The Flow, v0.0.1
Logging into the /ui/
Username = admin
Password = password
Features
Multiple User Accounts
- Users create their own account and you approve them. No need to fill out all the information yourself!
- Users can recover their own account. By setting up node-red-node-email and letting users get a new password; however email is not required users will just have to contact you to rest their password.
Restrict Tab access
- Just set the Tab number and access will only be granted to logged in users. If a user that is not logged in and clicks on a Restricted Tab they will be taken to the login page.
Basic User Account Control
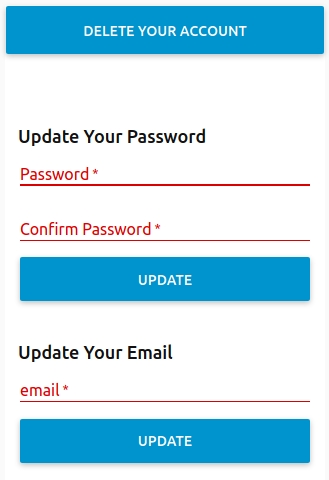
- Users can change their password after logging in. They can also delete their account.
Administrator
- Select a currently registered user and see information on the account. Then you may edit their role (admin/user), reset their password, or delete the user from the system.
- Select a pending user and and see their supplied information. The you can add the pending user or delete them.
- Password Requirements can be changed to make passwords more or less secure by requiring letters, numbers, or characters in a submitted password to meet requirements.
You can enable or disable email support for the user recovery of passwords. - See the Log and control its stored length.
- Enable/Disable email support for user account recovery.
- Control the LOG length and refresh it as needed.
Issues
Security
-
A user with a slow connection can get a load of the page before being redirected. BUT! because all triggers are tied to a socketid the user is unable to actually trigger a setting. It is recommended that any triggers and controls you create are tied to the socketid of the authorized user. Also a user would have to stop the page causing a 'lost' event for socket.io making them unable to control the page. upon reload he would be force redirected again.
-
socketid's are deleted upon connect and lost events. So if a user somehow managed to trick the server into accepting that he is of socketid of a currently logged in user then it would delete the socketid upon connect and force them to the login page.
-
ip addresses are tied to socketid's as well to be sure. Oh there are ways to spoof them but it adds another level.
-
Do I think its safe for the big bad world wide web. NO! But the mdashboard version solves all these issues of leaky pages. Sure they can get a blip of a page but its not populated with the data. Because all data shown is per socketid. I'm working on that version ATM and hope to release it next weekend.