Hello all,
After a year and a half of use I can say: well done to Node-RED devs and contributors, it is a wonderful piece of software. Thanks to it I have succeeded to fulfill my some-time-now dream to code after being given a project to develop a monitoring tool for my company.
And, thanks to this forum, the people have helped me (passively and actively) to overcome all problems (read: progress steps) I had.
Now, I have some more questions: 
-
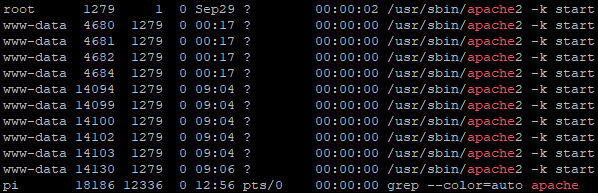
Recently my company started LAN screening for possible vulnerabilities, so, today they've told me they found vulnerabilities in my RevolutionPi-s - vulnerability with the Apache.
Some 15yrs ago I used to make some web programing using Apache as a server + PHP and MySQL, but I havent realized some of the current software runs on Apache? How to update it? (partial explanation in my question 2) -
My main Pi has got a Stretch linux from 12/2020 and I haven't updated anything since.
I am afraid an update will break something because I have lots of old (no updates avalible) aplications, such as:
- Mdashboard (stopped receiving updates in 2019)
- chromium-browser headless 32-bit (as far as I know this is outdated and replaced by a 64-bit version)
- mutt email client (not sure if anyone uses this anymore)
+Over 60 active mqtt connections, active sqlite storage which need to be accessible on demand and a regular PDF creation which my colleagues use daily.
Will I brake anything if I make:
?
sudo apt-get update
sudo apt-get upgrade
sudo apt-get dist-upgrade
- If want to disable the Pi access the internet - how to do it?
I need to be able to access it over a VPN.
So, I've tried:
- removed the DNS and gateway settings from the
/etc/dhcpcd.conffile - result was the Pi wasn't accessible over the VPN - removed only the DNS - result: Pi accessible but can also go to the internet and return a ping from a google
Is there any other possibility which would allow me to block it completely from the internet, but to be able to access it from a VPN?
- Local DNS service - is there any way (have anyone tried it?) to be able to enter only a name in the browser, instead of the full local IP addres+port+dashboard name?
I suppose a local DNS server is needed - can It be installed on the Pi itself? Not sure the IT admin would allow me to install in on company servers...
Thank you very much for all your help