Hi @Buckskin
Couple of years ago, I have been looking for a similar solution.
I did test various options, such as:
- Looping a ping, and also various deviates, such as hping or xping.
- Nmap, with various switches.
- Graphic tools, like Angry IP Scanner.
But none of these did really satisfy me.
At the end, I ended up with the command line tool of fing. (https://www.fing.com/).
Unfortunately this command line tool is not available anymore, but if someone is really interested. I still have the tool in RPM and DEB format, and also the documentation.
In this case send me a PM
I run this tool in a “Exec” node, and with a “Function” and “JSON” node it gives me the
desired result.
See the flow:
The last “Function” node is optional, because I use this to send the number of connected devices (equal to array length) to my Google Smart Home.
The result is as follows:
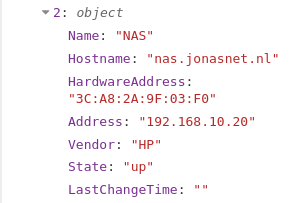
In this case, 52 devices are connected to my LAN.
Each element in the array shows the following (example)
Is this, what you prefer?
The flow:
[{"id": "26ac80fdb97288cc","type": "exec","z": "f447ccce.b9f9b8","command": "sudo fing -n 192.168.10.0/24 -r 1 -o table,json,console","addpay": false,"append": "","useSpawn": "false","timer": "","winHide": false,"oldrc": false,"name": "Scan Subnet","x": 410,"y": 100,"wires": [["cb228b6a37690cac"],,]},{"id": "daf82fd204f9e2e7","type": "inject","z": "f447ccce.b9f9b8","name": "Start Network Scan","props": [{"p": "payload"}],"repeat": "600","crontab": "","once": true,"onceDelay": 0.1,"topic": "","payload": "","payloadType": "date","x": 180,"y": 100,"wires": [["26ac80fdb97288cc"]]},{"id": "cb228b6a37690cac","type": "function","z": "f447ccce.b9f9b8","name": "Extract JSON string","func": "msg.payload = msg.payload.substring (msg.payload.indexOf("{"), msg.payload.lastIndexOf("}") + 1);\nreturn msg;","outputs": 1,"timeout": 0,"noerr": 0,"initialize": "","finalize": "","libs": ,"x": 640,"y": 100,"wires": [["30973414ac0fe1ea"]]},{"id": "30973414ac0fe1ea","type": "json","z": "f447ccce.b9f9b8","name": "JSON Object","property": "payload","action": "","pretty": false,"x": 870,"y": 100,"wires": [["da5afb34e823842e","7d25dfbf6eac665c"]]},{"id": "da5afb34e823842e","type": "function","z": "f447ccce.b9f9b8","name": "Number Connected Devices","func": "msg.payload = {\n "numConnectedDevices" : msg.payload.Hosts.length\n}\nreturn msg;","outputs": 1,"timeout": 0,"noerr": 0,"initialize": "","finalize": "","libs": ,"x": 1120,"y": 100,"wires": [["6ab9a0eb8880e5e8"]]},{"id": "6ab9a0eb8880e5e8","type": "link out","z": "f447ccce.b9f9b8","name": "To Google Home","mode": "link","links": ["e791a660cc5cbb04"],"x": 1315,"y": 100,"wires": },{"id": "7d25dfbf6eac665c","type": "debug","z": "f447ccce.b9f9b8","name": "debug 18","active": true,"tosidebar": true,"console": false,"tostatus": false,"complete": "false","statusVal": "","statusType": "auto","x": 1060,"y": 140,"wires": }]
Regards